基于Cisco的动态ACL、自反ACL配置
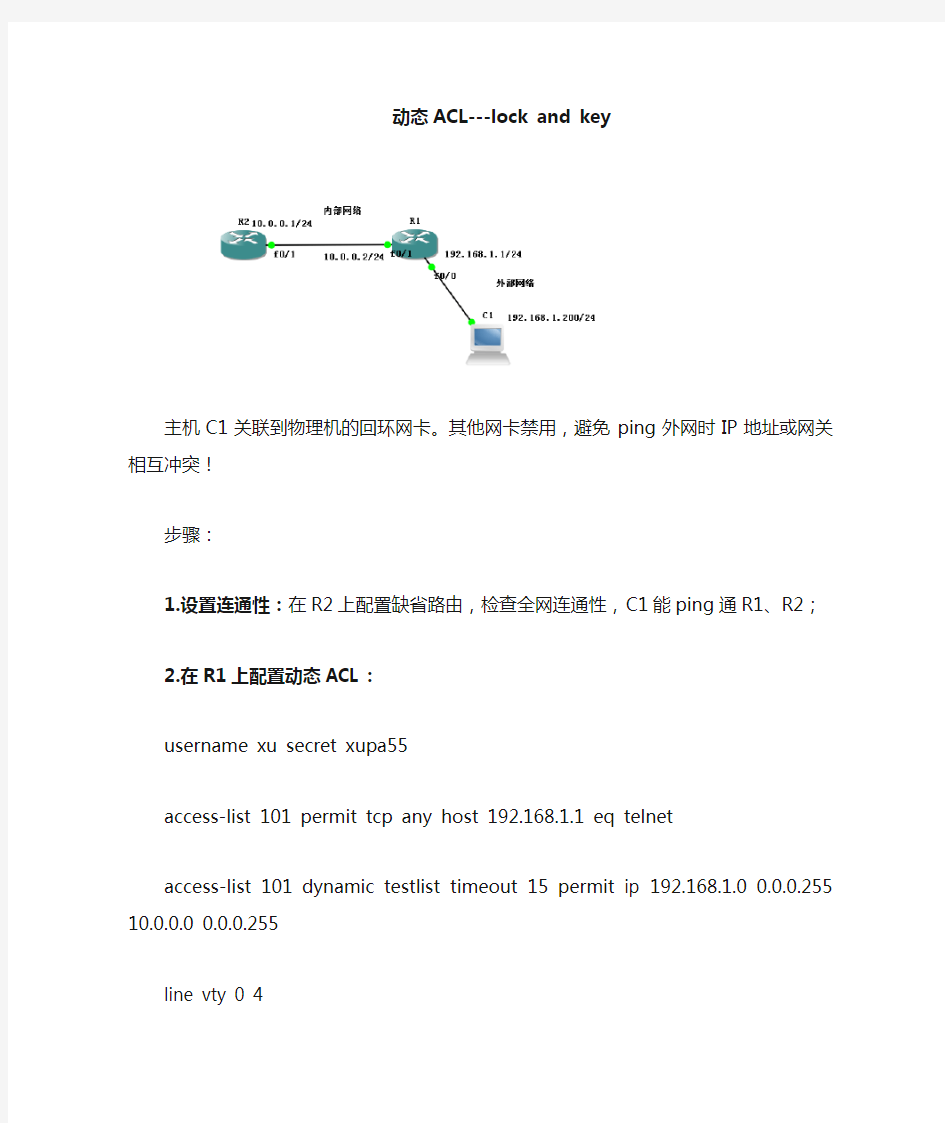

动态ACL---lock and key
主机C1关联到物理机的回环网卡。其他网卡禁用,避免ping外网时IP地址或网关相互冲突!
步骤:
1.设置连通性:在R2上配置缺省路由,检查全网连通性,C1能ping通R1、R2;
2.在R1上配置动态ACL:
username xu secret xupa55
access-list 101 permit tcp any host 192.168.1.1 eq telnet
access-list 101 dynamic testlist timeout 15 permit ip 192.168.1.0 0.0.0.255 10.0.0.0 0.0.0.255 line vty 0 4
login local
autocommand access-enable host timeout 5
3.验证配置结果
C1在telnet到R1之前,C1不能ping通R1、R2;
在C1在telnet到R1,通过验证后,telnet连接断开,ACL自动添加一条新的规则。
此时,再次尝试C1应该能ping通R1、R2;(证明通过验证后能访问内网了。)反复对比R1#show access-lists 101这条命令的执行结果,查看变化。
R1#show access-lists 101
Extended IP access list 101
10 permit tcp any host 192.168.1.1 eq telnet (93 matches)
20 Dynamic testlist permit ip 192.168.1.0 0.0.0.255 10.0.0.0 0.0.0.255
permit ip 192.168.1.200 0.0.0.255 10.0.0.0 0.0.0.255
自反ACL
主机C1关联到物理机的回环网卡。其他网卡禁用,避免ping外网时IP地址或网关相互冲突!
步骤:
1.设置连通性:在R2上配置缺省路由,检查全网连通性,C1能ping通R1、R2;
2.在R2上配置web服务:
username xua privilege 15 secret xuapa55
ip http server
ip http authentication local
3.在R1上配置自反ACL:
interface FastEthernet0/1
ip address 10.0.0.2 255.255.255.0
ip access-group external_ACL in
ip access-group internal_ACL out
!
ip access-list extended external_ACL
evaluate web-only-reflect-ACL
deny ip any any
ip access-list extended internal_ACL
permit tcp any any eq www reflect web-only-reflect-ACL
deny ip any any
4.验证结果(内部主机ping不通外部web服务器,但是可以用浏览器发起访问;外部ping不通内部,不允许外部发起的访问)
R1#sh access-lists internal_ACL
Extended IP access list internal_ACL
10 permit tcp any any eq www reflect web-only-reflect-ACL
20 deny ip any any (3 matches)
R1#sh access-lists external_ACL
Extended IP access list external_ACL
10 evaluate web-only-reflect-ACL
20 deny ip any any
R1#sh access-lists internal_ACL
Extended IP access list internal_ACL
10 permit tcp any any eq www reflect web-only-reflect-ACL
20 deny ip any any (6 matches)
R1#sh access-lists external_ACL
Extended IP access list external_ACL
10 evaluate web-only-reflect-ACL
20 deny ip any any
R1#sh access-lists external_ACL
Extended IP access list external_ACL
10 evaluate web-only-reflect-ACL
20 deny ip any any (12 matches)
R1#sh access-lists internal_ACL
Extended IP access list internal_ACL
10 permit tcp any any eq www reflect web-only-reflect-ACL (41 matches)
20 deny ip any any (6 matches)
R1#sh access-lists external_ACL
Extended IP access list external_ACL
10 evaluate web-only-reflect-ACL
20 deny ip any any (12 matches)
