思科路由器与华为路由器防火墙OSPF
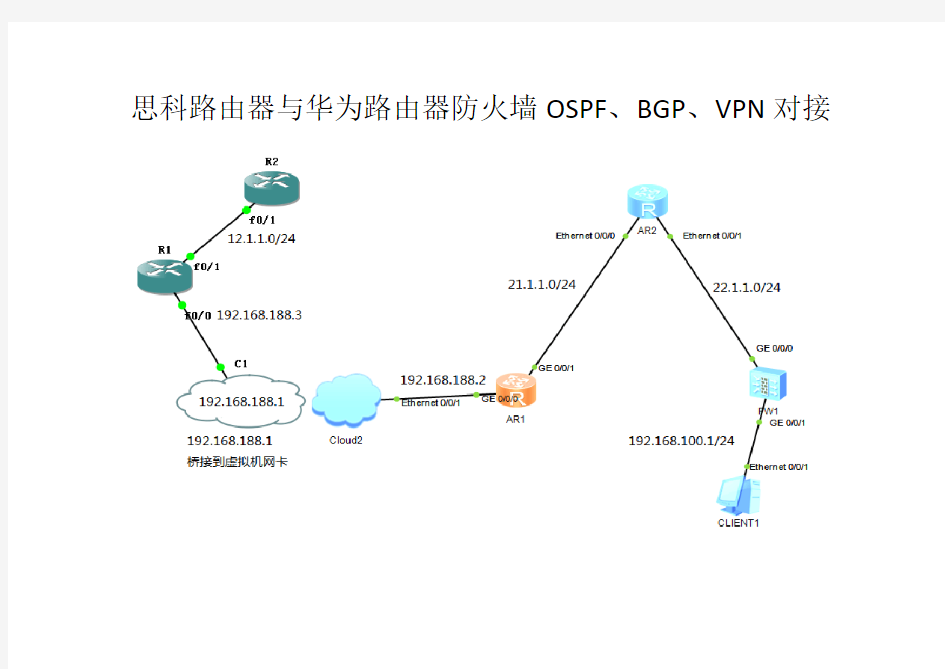

思科路由器与华为路由器防火墙OSPF、BGP、VPN对接
一.基本配置(按图标示在各接口配置IP)
思科路由器R2配置:
router ospf 100
log-adjacency-changes
network 12.1.1.2 0.0.0.0 area 0 Array三BGP对接(基本配置)
思科路由器配置:
router bgp 100
network 2.2.2.0 mask 255.255.255.0
neighbor 21.1.1.2 remote-as 200
neighbor 21.1.1.2 ebgp-multihop 255
no auto-summary
四.Site-to-site IPsec VPN
思科路由器配置:
crypto isakmp policy 1
en des 加密算法-des 与对端一致
hash md5 哈希算法-md5与对端一致
authentication pre-share 认证方式-共享密钥与对端一致
group 2 密钥算法-保证密钥安全与对端一致
crypto isakmp key 6 try789 address 22.1.1.2 设置共享密钥加密密码与对端一致
crypto ipsec transform-set ccnp esp-3des esp-md5-hmac ESP数据加密和哈希算法与对端一致crypto map ccnp 1 ipsec-isakmp
set peer 22.1.1.2
set transform-set ccnp
match address 100
ip nat inside source list 120 interface FastEthernet0/1 overload
access-list 100 permit ip 192.168.200.0 0.0.0.255 192.168.100.0 0.0.0.255 定义VPN感趣流,
access-list 120 deny ip 192.168.200.0 0.0.0.255 192.168.100.0 0.0.0.255 排除VPN流量,不进行NAT access-list 120 permit ip 192.168.200.0 0.0.0.255 any
!
华为防火墙配置:
acl number 3000
rule 5 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.200.0 0.0.0. 255 定义VPN感兴趣流ike proposal 100
en des
dh group2
authentication-algorithm md5
sa duration 5000
#
ike peer cisco
pre-shared-key try789
ike-proposal 100
remote-address 12.1.1.2
#
ipsec proposal cisco
esp encryption-algorithm 3des #
ipsec policy to_c 10 isakmp security acl 3000
ike-peer cisco
proposal cisco
#
interface GigabitEthernet0/0/0
alias GE0/MGMT
ip address 22.1.1.2 255.255.255.0 ipsec policy to_c
#
interface GigabitEthernet0/0/1
ip address 192.168.100.1 255.255.255.0 firewall zone trust
set priority 85
add interface GigabitEthernet0/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet0/0/0
ip route-static 0.0.0.0 0.0.0.0 22.1.1.1 #
policy interzone local untrust inbound policy 10
action permit
#
policy interzone local untrust outbound policy 10
action permit
policy source 22.1.1.2 0
#
policy interzone trust untrust inbound
policy 10
action permit
policy source 192.168.200.0 mask 24
policy destination 192.168.100.0 mask 24
#
policy interzone trust untrust outbound
policy 10
action permit
policy source 192.168.100.0 mask 24
#
nat-policy interzone trust untrust outbound nat-policy中policy no-nat在前,否则与ping不通对端的私有IP
policy 0
action no-nat
policy source 192.168.100.0 0.0.0.255 policy destination 192.168.200.0 0.0.0.255
policy 1
action source-nat
policy source 192.168.100.0 mask 24 easy-ip GigabitEthernet0/0/0
#
return
查看ike sa ipsec sa
R2#sh crypto isakmp sa
dst src state conn-id slot status 22.1.1.2 12.1.1.2 QM_IDLE 1002 0 ACTIVE
current ike sa number: 2
-----------------------------------------------------------------------------
conn-id peer flag phase vpn
-----------------------------------------------------------------------------
40004 12.1.1.2 RD v1:2 public 40001 12.1.1.2 RD v1:1 public
flag meaning
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT TD--DELETING NEG--NEGOTIATING D--DPD
